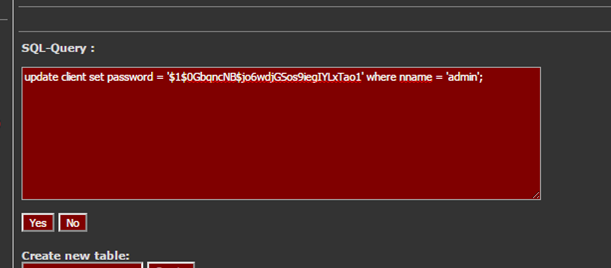
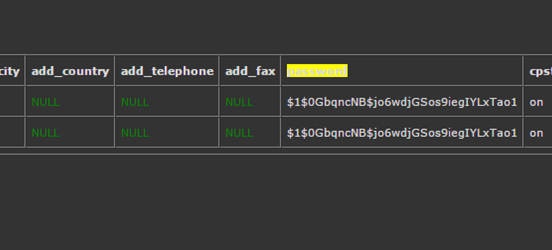
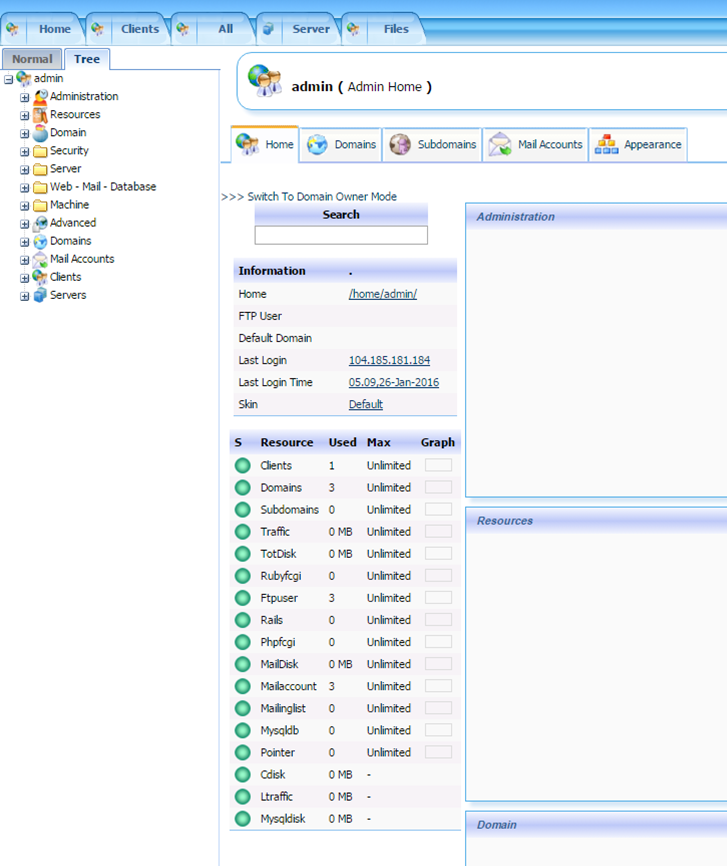
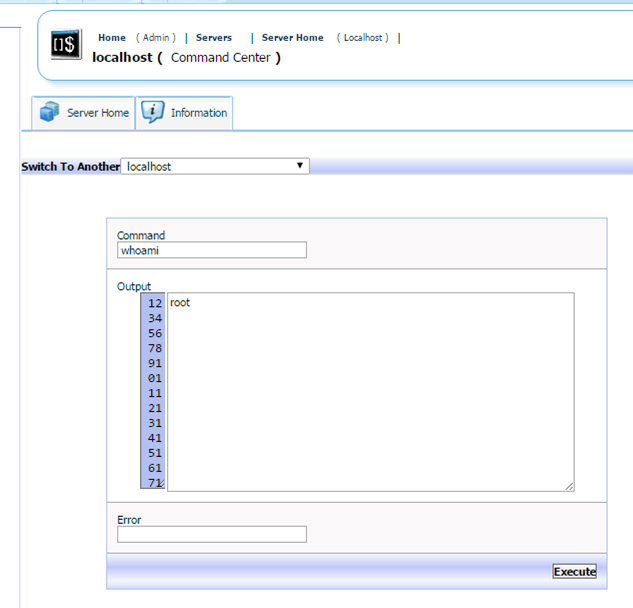
PalaceChat ( https://en.wikipedia.org/wiki/The_Palace_%28computer_program%29 ) is a classic program that was last updated in 2000, however it retains popularity today. Of course, being so old, configuring and using it on modern operating systems does require extra steps from the original installation instructions.
Modern operating system may be a bit of a misnomer as we are installing it on 32 bit Centos 5 in this guide. Any 64 bit versions of Centos or newer versions (such as 6 or 7) require even more changes which are much more complicated to make.
I recommend installing on Centos 5 32 bit as it will be the most straightforward way to get it running and this OS is available by almost all VPS / Server providers for provisioning.
Here is how you can install PalaceChat server in this type of setup:
First, ensure you are on the correct environment or else these instructions will not work:
[root@pchat2 bin]# uname -a
Linux pchat2.dotheneedful.in 2.6.32-042stab112.15 #1 SMP Tue Oct 20 17:22:56 MSK 2015 i686 athlon i386 GNU/Linux
[root@pchat2 bin]# cat /etc/redhat-release
CentOS release 5.11 (Final)
Here we can see we are on the 32 bit version (i686) and on Centos 5.11 so we can continue the installation
To start with lets verify all system software is up to date:
[root@pchat2 ]# yum update -y
Assuming yum is working correctly above, we need to ensure that no existing version of Apache is running on the server. This can be done using yum grouplist to check if apache (Web Server) is already installed and then remove it. I also removed some other groups that weren’t necessary to running a PalaceChat server:
[root@pchat2 installyumx86]# yum grouplist
Installed Groups:
DNS Name Server
Editors
Legacy Network Server
Mail Server
Network Servers
System Tools
Text-based Internet
Web Server
Windows File Server
Yum Utilities
Here we are removing groups, the one that must always be removed, if present, is “Web Server”
[root@pchat2 installyumx86]# yum groupremove “DNS Name Server” “Mail Server” “Windows File Server” “Web Server”
Now that the server environment is prepped, we can download the PalaceChat server software, I acquired it from http://www.palaceaholic.com/downloads.php
I recommend being in the /root directory to perform this:
[root@pchat2 ]# cd /root
Now we can download the Software:
[root@pchat2 ~]# wget http://www.palaceaholic.com/downloads/server/linux/PalaceServerLinux.tar.gz
2016-01-11 21:05:26 (1.11 MB/s) – `PalaceServerLinux.tar.gz’ saved [1076324/1076324]
Extract the Software you downloaded:
[root@pchat2 ~]# tar -xzvf PalaceServerLinux.tar.gz
pserver-4.5.1.i686-unknown-linux/
pserver-4.5.1.i686-unknown-linux/MANIFEST
pserver-4.5.1.i686-unknown-linux/RELNOTES
pserver-4.5.1.i686-unknown-linux/install
pserver-4.5.1.i686-unknown-linux/license.txt
pserver-4.5.1.i686-unknown-linux/setup
pserver-4.5.1.i686-unknown-linux/arch.tar
pserver-4.5.1.i686-unknown-linux/frame.tar
pserver-4.5.1.i686-unknown-linux/instance.tar
And enter the pserver directory:
[root@pchat2 ~]# cd pserver-4.5.1.i686-unknown-linux/
Once in the directory, start the palaceserver installation:
[root@pchat2 pserver-4.5.1.i686-unknown-linux]# ./install
I recommend using all defaults:
Default location (press return) is: [/usr/local/palace]
Now, the PalaceServer asks for a license key; Apparently there are places online you can generate a unique key, however I couldn’t locate one quickly. I did find a key left in a thread here: http://pchat.org/support/#/discussion/299/question-for-pawn-or-anyone-who-can-answer-this
License number:
6DV3K-PVY6F-RF2VT-QFG8S
Configure a few more options on the setup, replacing the values with your data of course:
(e.g. yourserver.domain.com):
pchat.dotheneedful.in
Default Palace Server port (press return) is: [9998]
Default HTTP Server port (press return) is: [9990]
PalaceServer Name:
pchat
It is important to select no when the setup asks if you wish to start the server; it will not run without further changes being made:
The server is now installed. Would you like to start it now?
no
Lets enter the PalaceServer’s directory:
[root@pchat2 pserver-4.5.1.i686-unknown-linux]# cd /usr/local/palace/bin
To see what exactly we need to do to get PalaceServer running, lets try starting it manually. This is optional, of course on your end:
[root@pchat2 bin]# bash start-httpd
start-httpd: /usr/local/palace/bin/httpd: /lib/ld-linux.so.1: bad ELF interpreter: No such file or directory
This is happening as the pre-compiled version of apache included with PalaceServer cannot run on Centos 5 without changes. Here is where we start to deviate from the original installation process. As we have to compile Apache 1.3 (the version that PalaceServer integrates with) manually, make sure you have a compiler installed:
[root@pchat2 bin]# yum install gcc -y
Installed:
gcc.i386 0:4.1.2-55.el5
Now we need to acquire the source for Apache 1.3, I found a version here I could download: http://olex.openlogic.com/packages/apache/1.3.31 and then saved it to my /root folder.
Lets ensure we are back in /root:
[root@pchat2 bin]# cd /root
Extract your Apache 1.3 archive:
[root@pchat2 ~]# unzip apache-1.3.31-all-src.zip
Enter the extracted folder:
[root@pchat2 ~]# cd apache-1.3.31-src
To be able to compile Apache 1.3 we need to ensure the relevant executables have appropriate permissions. While you can do this in a much more restrictive way, this was the fastest way to ensure everything was set right:
[root@pchat2 apache-1.3.31-src]# chmod a+x * -R
Now, we need to configure the Apache 1.3 source:
[root@pchat2 apache-1.3.31-src]# ./configure
Configuring for Apache, Version 1.3.31
+ Warning: Configuring Apache with default settings.
+ This is probably not what you really want.
+ Please read the README.configure and INSTALL files
+ first or at least run ‘./configure –help’ for
+ a compact summary of available options.
+ using installation path layout: Apache (config.layout)
Creating Makefile
Creating Configuration.apaci in src
Creating Makefile in src
+ configured for Linux platform
+ setting C compiler to gcc
+ setting C pre-processor to gcc -E
+ using “tr [a-z] [A-Z]” to uppercase
+ checking for system header files
+ adding selected modules
+ using builtin Expat
+ checking sizeof various data types
+ doing sanity check on compiler and options
Creating Makefile in src/support
Creating Makefile in src/regex
Creating Makefile in src/os/unix
Creating Makefile in src/ap
Creating Makefile in src/main
Creating Makefile in src/lib/expat-lite
Creating Makefile in src/modules/standard
Once done, run make:
[root@pchat2 apache-1.3.31-src]# make
Once that finishes run make install. Assuming it compiles on your system you should receive a success message at the end:
[root@pchat2 apache-1.3.31-src]# make install
+——————————————————–+
| You now have successfully built and installed the |
| Apache 1.3 HTTP server. To verify that Apache actually |
| works correctly you now should first check the |
| (initially created or preserved) configuration files |
| |
| /usr/local/apache/conf/httpd.conf
| |
| and then you should be able to immediately fire up |
| Apache the first time by running: |
| |
| /usr/local/apache/bin/apachectl start
| |
| Thanks for using Apache. The Apache Group |
| http://www.apache.org/ |
+——————————————————–+
Lets go back to the Palace Directory:
[root@pchat2 apache-1.3.31-src]# cd /usr/local/palace/bin
And replace Palace’s included httpd with our newly compiled version:
[root@pchat2 bin]# cp /usr/local/apache/bin/httpd /usr/local/palace/bin/httpd
cp: overwrite `/usr/local/palace/bin/httpd’? y
Lets try starting it again using the same script as before:
[root@pchat2 bin]# ./start-httpd
Wait a few seconds and then you can verify if it has started through ps. We can see it did start successfully:
[root@pchat2 bin]# ps faux | grep httpd
root 3811 0.0 0.1 3112 708 pts/0 S+ 21:13 0:00 \_ grep httpd
root 3806 0.0 0.1 2728 828 ? Ss 21:13 0:00 /usr/local/palace/bin/httpd -f /usr/local/palace/conf/httpd.conf
nobody 3807 0.0 0.0 2728 508 ? S 21:13 0:00 \_ /usr/local/palace/bin/httpd -f /usr/local/palace/conf/httpd.conf
nobody 3808 0.0 0.0 2728 508 ? S 21:13 0:00 \_ /usr/local/palace/bin/httpd -f /usr/local/palace/conf/httpd.conf
nobody 3809 0.0 0.0 2728 508 ? S 21:13 0:00 \_ /usr/local/palace/bin/httpd -f /usr/local/palace/conf/httpd.conf
Now lets start the Palace Server too:
[root@pchat2 bin]# ./start-palace
And verify it is running as well:
[root@pchat2 bin]# ps faux | grep pserv
root 3827 0.0 0.1 3112 712 pts/0 S+ 21:13 0:00 \_ grep pserv
root 3822 0.0 0.3 3176 2012 pts/0 S 21:13 0:00 /usr/local/palace/bin/pserver -f /usr/local/palace/palace/psdata/pserver.conf
root 3823 0.0 0.1 1820 560 pts/0 S 21:13 0:00 \_ /usr/local/palace/bin/psfront -p 9998 -r /usr/local/palace/palace -l logs/pserver.log -s 0 -a localhost -n -b 0.0.0.0 -c 10
root 3824 0.0 0.1 2120 936 pts/0 S 21:13 0:00 | \_ /usr/local/palace/bin/psfront -p 9998 -r /usr/local/palace/palace -l logs/pserver.log -s 0 -a localhost -n -b 0.0.0.0 -c 10
root 3825 0.0 0.2 2780 1240 pts/0 S 21:13 0:00 \_ /usr/local/palace/bin/pserver -f /usr/local/palace/palace/psdata/pserver.conf
If you wish to verify even further the services are listening you can do that via Telnet:
[root@pchat2 logs]# telnet localhost 9998
Trying 127.0.0.1…
Connected to localhost.
Escape character is ‘^]’.
ryit
[root@pchat2 logs]# curl localhost:9990 –head
HTTP/1.1 200 OK
Now, PalaceServer is successfully installed and running; of course you will still need to configure your server but the original documentation will suffice for that.
Please note that Apache 1.3 is very old software (as well as PalaceChat). Apache 1.3 has known vulnerabilities and it is not recommended to use this in a production environment. If you wish to host a production server I recommend using Apache 2.4 instead and updating PalaceChat’s httpd.conf file to work with this newer Apache version.